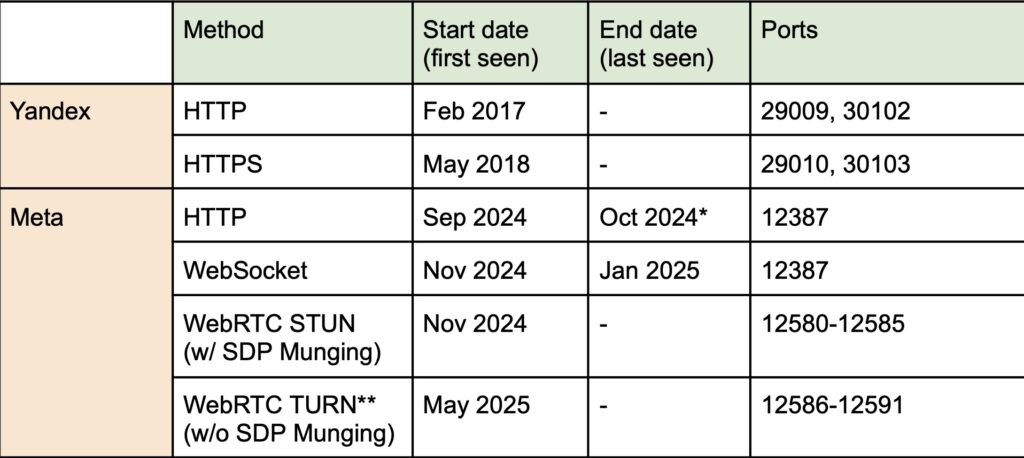
An outline of Yandex identifier sharing
A timeline of net historical past monitoring by Meta and Yandex
Some browsers for Android have blocked the abusive JavaScript in trackers. DuckDuckGo, as an example, was already blocking domains and IP addresses related to the trackers, stopping the browser from sending any identifiers to Meta. The browser additionally blocked many of the domains related to Yandex Metrica. After the researchers notified DuckDuckGo of the unfinished blacklist, builders added the lacking addresses.
The Courageous browser, in the meantime, additionally blocked the sharing of identifiers attributable to its in depth blocklists and present mitigation to block requests to the localhost with out express person consent. Vivaldi, one other Chromium-based browser, forwards the identifiers to native Android ports when the default privateness setting is in place. Altering the setting to dam trackers seems to thwart looking historical past leakage, the researchers stated.
Monitoring blocker settings in Vivaldi for Android.
There’s received to be a greater means
The assorted cures DuckDuckGo, Courageous, Vivaldi, and Chrome have put in place are working as supposed, however the researchers warning they may change into ineffective at any time.
“Any browser doing blocklisting will seemingly enter into a relentless arms race, and it is only a partial answer,” Vallina Rodriguez stated of the present mitigations. “Creating efficient blocklists is tough, and browser makers might want to continuously monitor the usage of one of these functionality to detect different hostnames probably abusing localhost channels after which updating their blocklists accordingly.”
He continued:
Whereas this answer works as soon as you recognize the hostnames doing that, it isn’t the appropriate means of mitigating this challenge, as trackers could discover methods of accessing this functionality (e.g., by means of extra ephemeral hostnames). A protracted-term answer ought to undergo the design and growth of privateness and safety controls for localhost channels, in order that customers can pay attention to one of these communication and probably implement some management or restrict this use (e.g., a permission or some comparable person notifications).
Chrome and most different Chromium-based browsers executed the JavaScript as Meta and Yandex supposed. Firefox did as properly, though for causes that are not clear, the browser was not in a position to efficiently carry out the SDP munging laid out in later variations of the code. After blocking the STUN variant of SDP munging within the early Might beta launch, a manufacturing model of Chrome launched two weeks ago started blocking each the STUN and TURN variants. Different Chromium-based browsers are more likely to implement it within the coming weeks. Firefox did not reply to an electronic mail asking if it has plans to dam the conduct in that browser.